Certificates
In USP certificates are essential for securing TLS-based communication between USP components and external systems. Certificates enable identity verification and trust validation during mutual TLS (mTLS) authentication and other TLS-secured interactions.
USP uses two types of certificates:
- TLS Certificates are used by the USP Manager, USP Server, and external services (such as LDAP servers) to present their identity during a TLS handshake.
- CA Certificates are used to validate the TLS Certificates presented by remote systems, ensuring they were issued by a trusted authority.
For information on how to create these certificates, refer to mTLS Certificates Generation Guide.
How USP Uses Certificates
Certificates are used in the following scenarios:
| Scenario | Description | Context |
|---|---|---|
| USP Manager and USP Server mTLS Authentication | Used to authenticate and encrypt communication between the USP Manager and USP Server through mutual TLS (mTLS). | System interconnection (between USP components) |
| Inbound FTPS/HTTPS Server Identity Verification | Used by USP Server to authenticate itself to external incoming clients and validate the client's identity during the TLS handshake. | FTPS and HTTPS (business file transfers) |
| Outbound FTPS/HTTPS Target Verification | Used by USP Server to authenticate itself to the internal target and validate the target's TLS Certificate during the TLS handshake. | FTPS and HTTPS (business file transfers) |
| LDAP Server Identity Validation | Used to verify the TLS Certificate presented by an external LDAP server when authenticating inbound users via LDAP over SSL/TLS. | Authentication at the Proxy |
USP Manager and USP Server mTLS Authentication
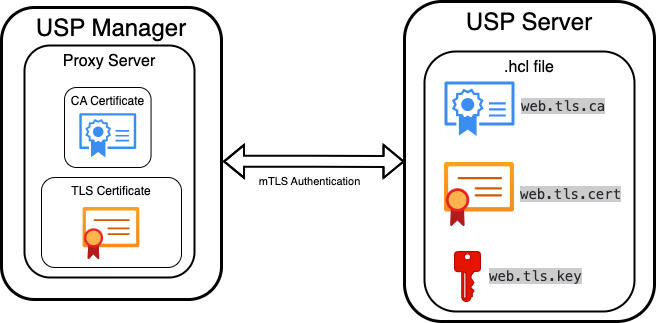
To enable secure and authenticated communication, the USP Manager and USP Server components use mutual TLS (mTLS). This process requires two sets of:
- A TLS Certificate to assert the component's identity.
- A private key to prove ownership of the TLS Certificate.
- A CA Certificate to verify the identity of the remote peer.
This mutual validation ensures that only authorized components can establish a secure connection within USP.
- USP Manager Side
- USP Server Side
From the USP Manager perspective, a CA Certificate and a TLS Certificate are selected when adding a Proxy Server:
- CA Certificate: Validates the TLS Certificate presented by the USP Server.
- TLS Certificate: Identifies the USP Manager when it connects to the USP Server.
Before they can be selected in a Proxy Server configuration, CA Certificates and TLS Certificates must be added to the USP Manager repository.
On the USP Server side, a TLS Certificate, its corresponding private key, and a CA Certificate are configured directly in the USP Server Configuration File:
web.tls.cert: Path to the TLS Certificate presented by the USP Server.web.tls.key: Path to the private key associated with the TLS Certificate.web.tls.ca: Path to the CA Certificate used to validate the TLS Certificate presented by the USP Manager.
If you need help generating these certificates, refer to our mTLS Certificates Generation Guide.
Inbound FTPS/HTTPS Server Identity Verification
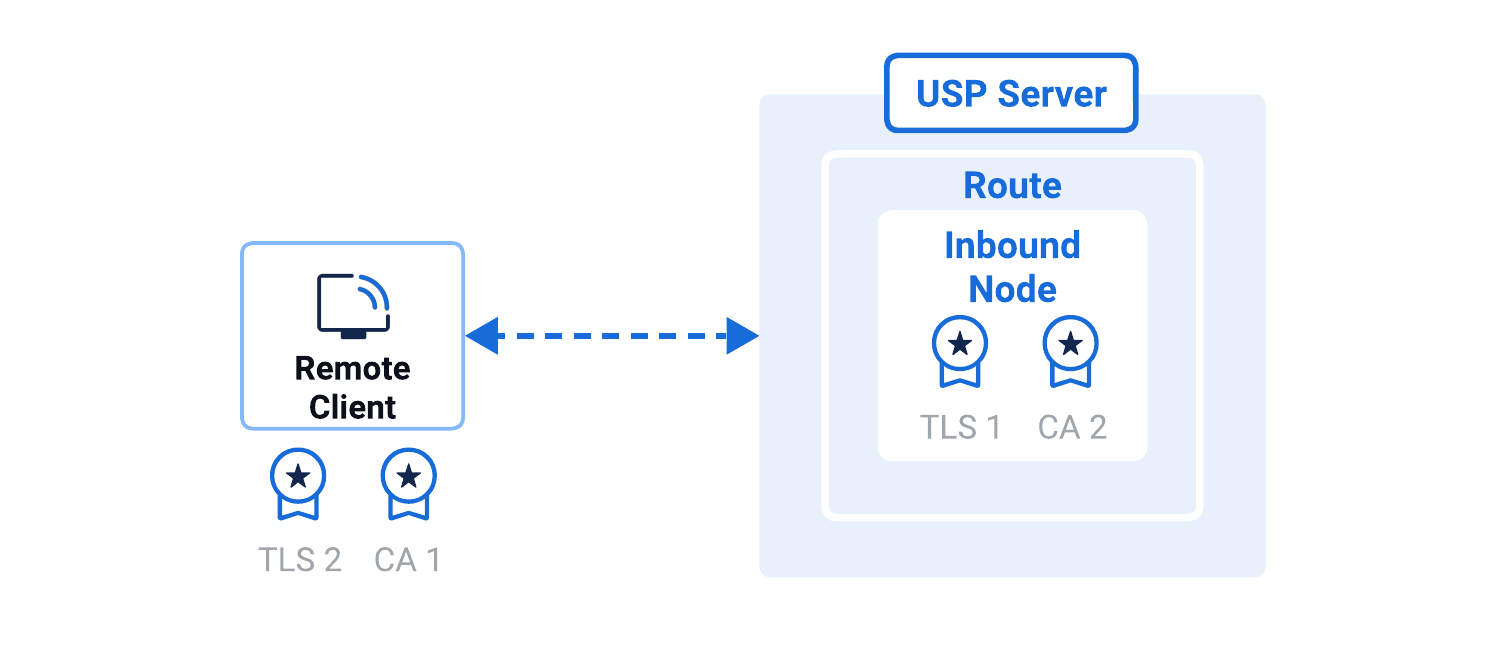
Both FTP and HTTP protocols can optionally use TLS to secure communication channels.
When TLS is enabled, the USP Server acts as the TLS server, presenting its TLS Certificate to external clients so they can verify its identity.
- TLS Certificate: Set when adding an Inbound Node. Identifies the USP Server to external clients during the TLS handshake.
- CA Certificate: Set when adding an Inbound Node. Validates the TLS Certificate presented by an external client, if client authentication is enabled.
If a TLS Certificate is provided, TLS encryption is enabled for the connection.
If a CA Certificate is also specified, USP enforces mutual TLS (mTLS), requiring both sides to present and validate certificates.
If no certificates are specified, the connection defaults to plain FTP or HTTP with no encryption.
Outbound FTPS/HTTPS Target Verification
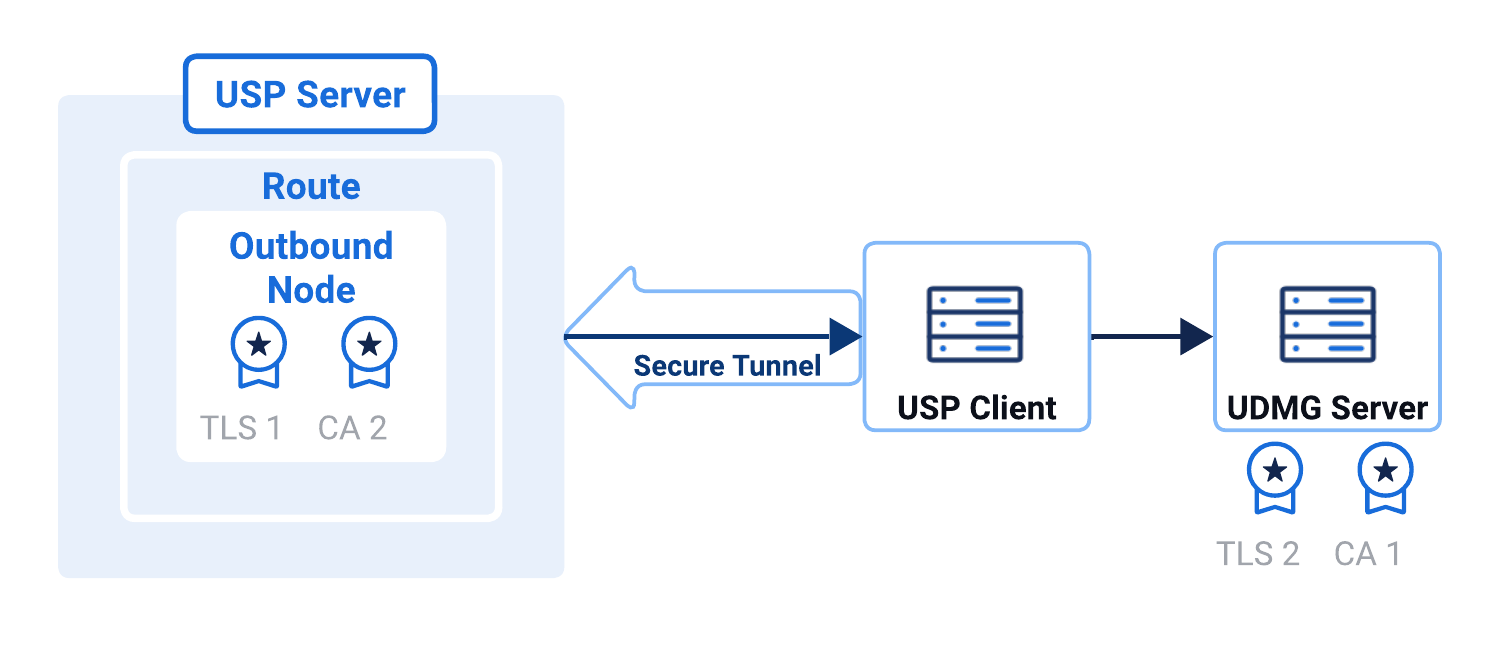
Both FTP and HTTP protocols can optionally use TLS to secure outbound connections between the USP Server and internal target systems.
When mTLS is enabled, the USP Server acts as the TLS client, presenting its TLS Certificate to the target and validating the target's certificate using the configured CA Certificate.
- CA Certificate: Set when adding an Outbound Node. Validates the TLS Certificate presented by the internal target to ensure it was issued by a trusted authority.
- TLS Certificate: Set when adding an Outbound Node. Identifies the USP Server to the internal target during the TLS handshake.
If a CA Certificate is provided, TLS encryption is enabled for the connection.
If a TLS Certificate is also specified, USP enforces mutual TLS (mTLS), requiring both the USP Server and the internal target to present and validate certificates.
If no certificates are specified, the connection defaults to plain FTP or HTTP with no encryption.
LDAP Server Identity Validation
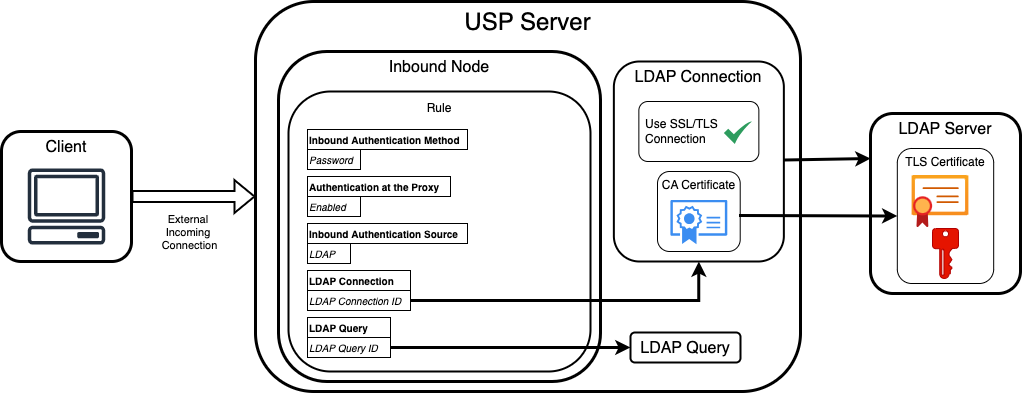
When a Rule is configured with Inbound Authentication Method set to Password, Authentication at the Proxy enabled, and Inbound Authentication Source set to LDAP, the USP Server authenticates inbound credentials against an external LDAP directory. This process relies on two components: an LDAP Connection and an LDAP Query.
If the LDAP Connection is configured to use SSL/TLS, a CA Certificate is required to validate the TLS Certificate presented by the LDAP server. This ensures that the USP Server connects only to a trusted LDAP endpoint before transmitting credentials.
Summary
To use a CA Certificate to validate the TLS Certificate presented by the LDAP server, the Rule must be set with the following:
- Inbound Authentication Method: Password
- Authentication at the Proxy: Enabled
- Inbound Authentication Source: LDAP
- LDAP Connection, with:
- Use SSL/TLS Connection: Enabled
- CA Certificate: A CA Certificate that matches the issuer of the LDAP server's TLS Certificate
- LDAP Query: An LDAP Query to locate and validate user entries in the directory