Overview
UDMG Secure Proxy (USP) is an advanced reverse-proxy solution designed to work alongside Stonebranch's Universal Data Mover Gateway (UDMG), a powerful Managed File Transfer (MFT) platform. USP enables external partners to initiate secure file transfers into your internal network, without exposing internal systems directly or requiring any inbound firewall openings.
This architecture is tailored for security-sensitive environments where hosting UDMG in a demilitarized zone (DMZ) is not permitted.
USP Key Features
- Reverse Proxy for Secure File Transfers
USP sits in front of internal systems and brokers all file transfer traffic, acting as an intermediary between external users and UDMG. - Session Break Security Model
Inbound connections are terminated in the DMZ by the USP Server. Only after successful authentication of the inbound connection, a new outbound connection is initiated by the USP Server into the internal target in the LAN, ensuring complete isolation between external and internal networks. - No Inbound Firewall Rules
Traffic from the DMZ to the LAN is initiated by the LAN-hosted USP Client and forwarded over a secure tunnel, maintaining a strict one-way network flow that eliminates exposure, and removing the need to allow traffic from the DMZ into the LAN. - Multiple Authentication Mechanisms
USP supports a flexible authentication architecture using LDAP, Account Repositories, or pass-through credentials from the inbound connection.
Session Break
At the core of USP is the Session Break mechanism, a security model that ensures full isolation between the external user and internal resources. This feature terminates and optionally pre-authenticates (see Deployment Models) external sessions in the DMZ before securely relaying them to UDMG through a tunnel originated within the internal network.
This separation ensures that:
- UDMG remains isolated behind a firewall.
- All inbound traffic is terminated at the DMZ and authenticated before any outbound connection is made to the LAN.
How It Works
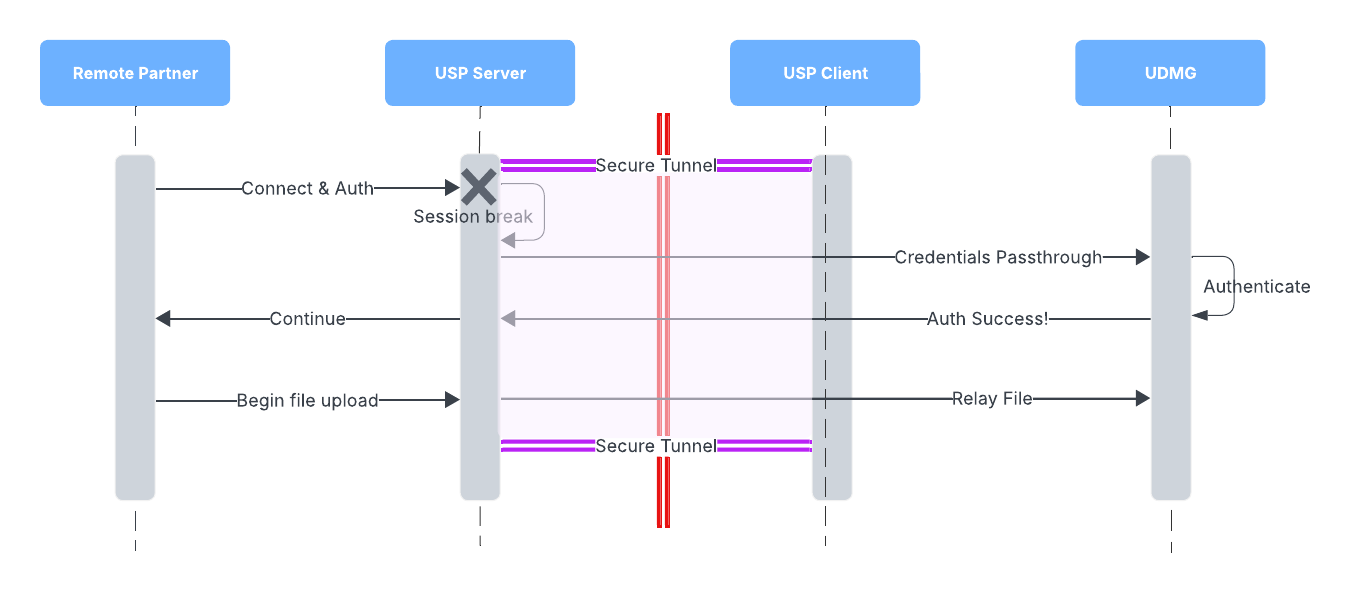
- An External Partner connects to the USP Server and attempts authentication.
- The USP Server, hosted in the DMZ, terminates the connection, authenticates it, and finally, requests a connection to the internal target to the USP Client.
- The USP Client securely forwards the connection to the USP Server.
- Upon successful authentication, the USP Server establishes a session break between the inbound and outbound connections.
- There is no direct connection between the external partner and internal systems.