System Architecture
The UDMG Secure Proxy (USP) is Stonebranch's proxy solution for secure, policy-driven connectivity between external clients and internal targets. It provides a strong session break at the network edge, preventing direct connections into the LAN and enforcing authentication before traffic is forwarded.
When paired with Universal Data Mover Gateway (UDMG), the solution delivers end-to-end security and control for managed file transfers. USP enforces authentication and isolation at the edge, while UDMG manages transfer orchestration, partner provisioning, and policy enforcement within the internal network.
While USP provides strong security controls, including full session-break and optional authentication at the edge, UDMG manages core transfer logic, policy enforcement, partner provisioning, and pre/post transaction orchestration.
Together, the combined UDMG + USP solution enables a zero-trust architecture for modern file transfer workflows, reinforcing a defense-in-depth approach that meets the security and scalability demands of the modern enterprise.
The diagram below illustrates a standard deployment architecture across three network zones:
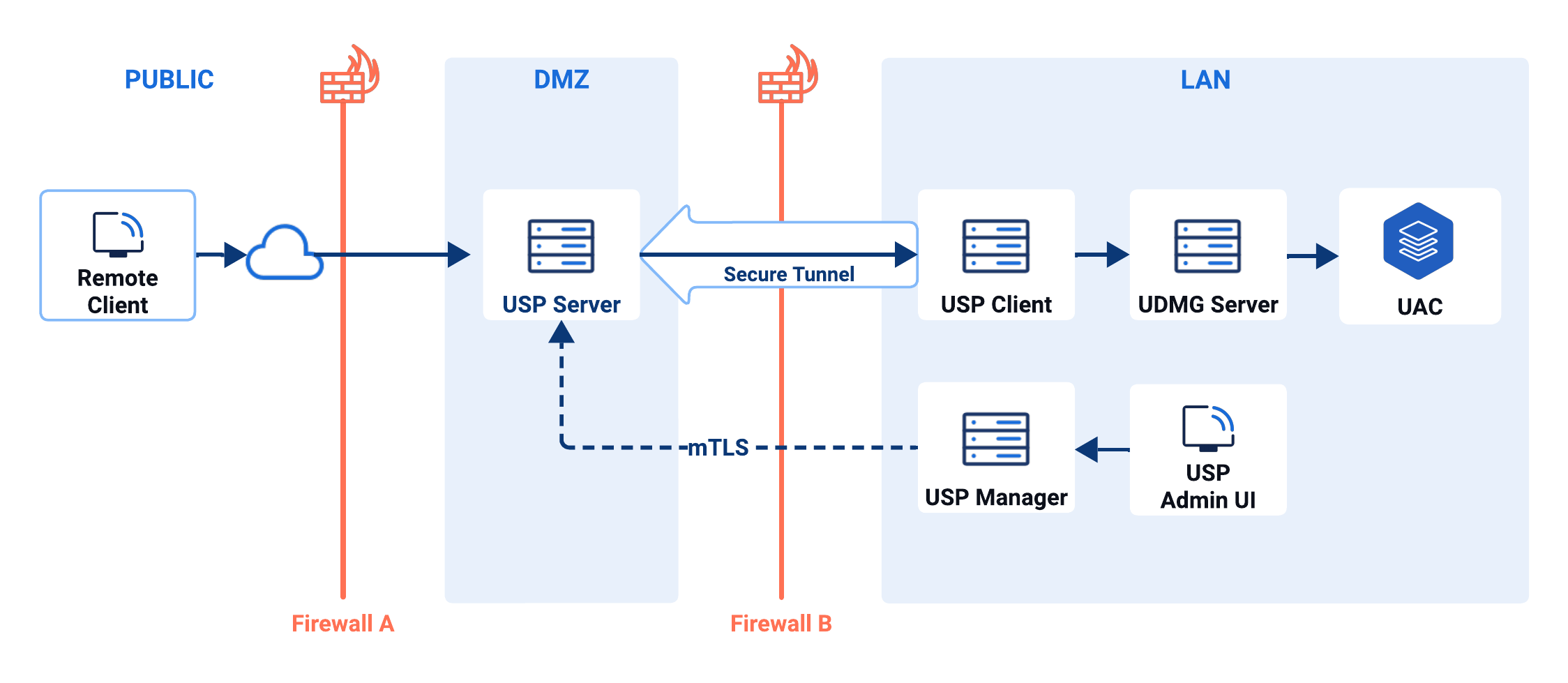
The diagram above shows a basic deployment with a single instance of each USP component. For production environments that require zero downtime, we recommend using a high-availability deployment.
Diagram Overview
| Zone | Item | Role |
|---|---|---|
| Public | Remote Client | Initiates file transfers to the USP Server instance from an external network. Represents a business partner or external system. |
| DMZ | Firewall A | Controls inbound traffic from the public zone to the DMZ, allowing only specific ports and IP ranges to reach approved services such as USP Server. |
| USP Server | Terminates all inbound connections from external clients and maintains a secure tunnel with the USP Client, providing full session break and preventing direct access to the LAN. | |
| LAN (Trusted Internal Network) | Firewall B | Secures the internal LAN by permitting only outbound connections. |
| USP Client | Initiates a secure tunnel to the USP Server and securely forwards requests to the UDMG Server. | |
| USP Manager | Centrally manages the USP Server instance, communicating over mutual TLS (mTLS). info As USP Manager stores mTLS and other sensitive credentials, it should be deployed in a secure network—typically the internal LAN—and not in the DMZ. | |
| USP Admin UI | USP Manager's web-based interface used to configure and monitor USP Server instances, including listeners, tunnels, and credentials. | |
| USP Database | Stores configuration, metadata, and operational data used by the USP Manager. | |
| UDMG Server | Orchestrates transfer workflows and interacts with the UDMG database for configuration and transactional data. | |
| UAC | When configured, UDMG can generate events on file transfer completion or failure. These events are pushed to Universal Automation Center (UAC), enabling automated workflows and enterprise-wide integrations. |
Component Breakdown
USP Server
USP Server is the core component responsible for enforcing a secure boundary between external clients and internal systems. Deployed in the DMZ, it terminates inbound connections and establishes a full session break, preventing direct traffic into the LAN.
It authenticates external connections, applies routing rules, and forwards only validated traffic into the trusted network. When firewall restrictions prevent direct access, the USP Server communicates with USP Client instances to reach internal targets securely.
USP Client
USP Client is deployed in the trusted internal network (LAN). It establishes a secure tunnel back to the USP Server, enabling access to internal systems that would otherwise be unreachable due to firewall restrictions.
Once a connection is authenticated and authorized by the USP Server, the USP Client forwards the traffic securely to the designated UDMG Server or other internal targets.
USP Manager
USP Manager provides centralized control over USP Server instances. It is typically deployed in the LAN and communicates with USP Servers via mutual TLS (mTLS) to ensure confidentiality and authenticity.
USP Manager pushes validated configurations to USP Servers, tracks their operational state, and ensures version-controlled updates. This central management component allows administrators to enforce consistent policies across distributed USP deployments.
USP Admin UI
USP Admin UI is a browser-based interface for administrators to configure and monitor USP Server instances. Accessible through USP Manager, it provides a secure and intuitive way to manage listeners, tunnels, authentication rules, certificates, accounts, and deployment state. The USP Admin UI centralizes all management tasks, enabling administrators to oversee the entire proxy infrastructure without requiring direct access to servers in the DMZ.
UDMG Server
UDMG Server is deployed in the trusted internal network (LAN) to deliver enterprise-grade Managed File Transfer (MFT) capabilities. It consists of three primary components: UDMG Server, UDMG Database, and the UDMG Admin UI.
Together, the UDMG components provide:
- Centralized orchestration of file transfer workflows.
- Secure credential, endpoint, and pipeline management.
- Event-driven automation through UAC integration.
For a detailed view of USP's companion Managed File Transfer platform, refer to UDMG documentation.
UAC
Universal Automation Center (UAC) integrates with UDMG to provide enterprise-scale automation capabilities. When configured, UDMG can generate events on file transfer completion or failure. These events are published to UAC as Universal Events and can trigger Tasks in UAC, enabling automated workflows and enterprise-wide integrations.
This integration enables administrators to orchestrate downstream workflows that respond automatically to file movement, such as validation, enrichment, notification, or integration with other enterprise systems. By combining UDMG's secure file transfer capabilities with UAC's scheduling and automation, organizations can create fully automated, event-driven data pipelines.
For a detailed view of Stonebranch's automation companion, refer to UAC documentation.