Deployment Models
UDMG Secure Proxy (USP) can be tailored to support different deployment scenarios depending on your organization's security posture, infrastructure layout, and operational needs. These scenarios, comprising specific combinations of Components and Configuration, are referred to as Deployment Models.
This page outlines two recommended deployment models in detail, briefly introduces one additional model, and provides considerations for choosing the best approach.
Recommended Deployment Models
Model 1: Double Authentication with Credential Passthrough
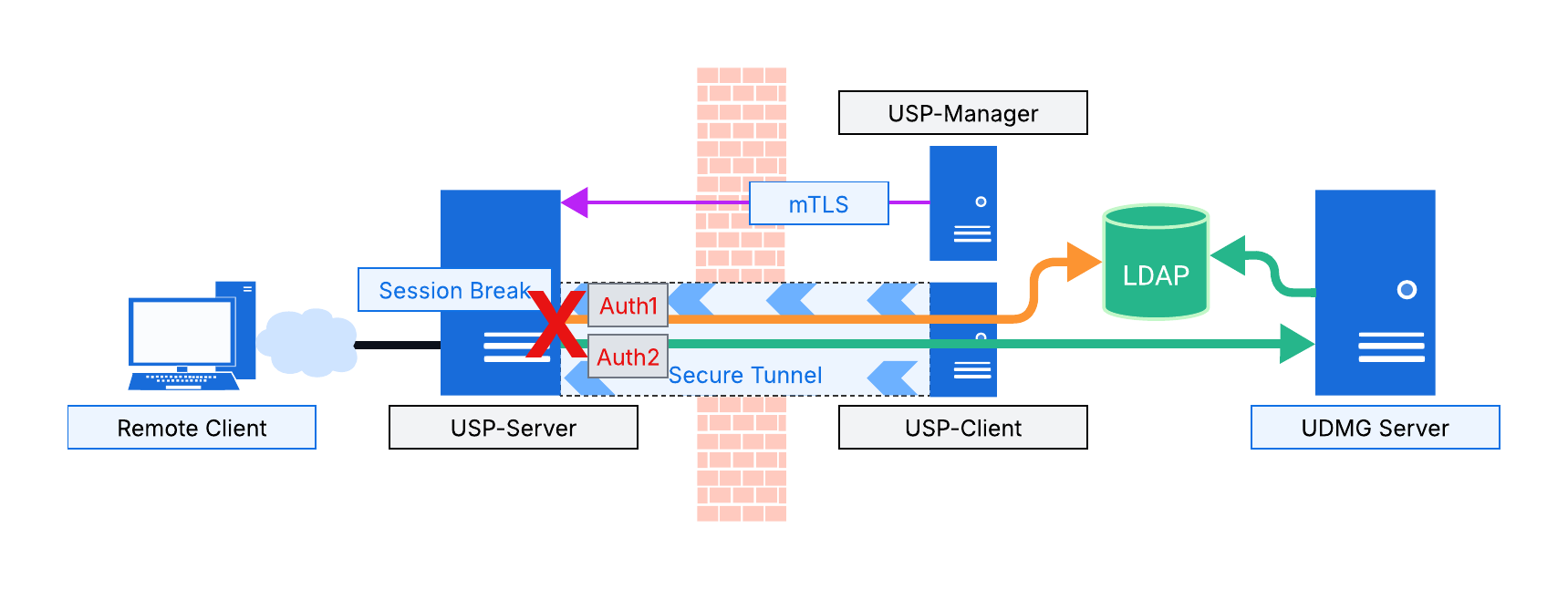
In this model, all three USP components (USP Manager, USP Server, and USP Client) are used (see Note on Minimal Installations).
The USP Server, deployed in the DMZ and configured via the USP Manager, performs authentication of external inbound connections. The provided credentials can be validated against a local Account Repository, or against an LDAP directory server (orange arrow), which could reside in the LAN (the latter example illustrated above).
Once the first authentication is successful, the USP Server then connects to the internal UDMG Server in the LAN via a secure tunnel established by the USP Client, also residing somewhere in the LAN, and relays (passes through) the client-provided credentials for authentication with UDMG Server (as illustrated in this example, against the same LDAP directory).
| Use Case | Benefits | Drawbacks |
|---|---|---|
| High-security environments where external clients must be validated before reaching internal systems. |
|
|
Model 2: No Pre-Authentication with Credential Passthrough
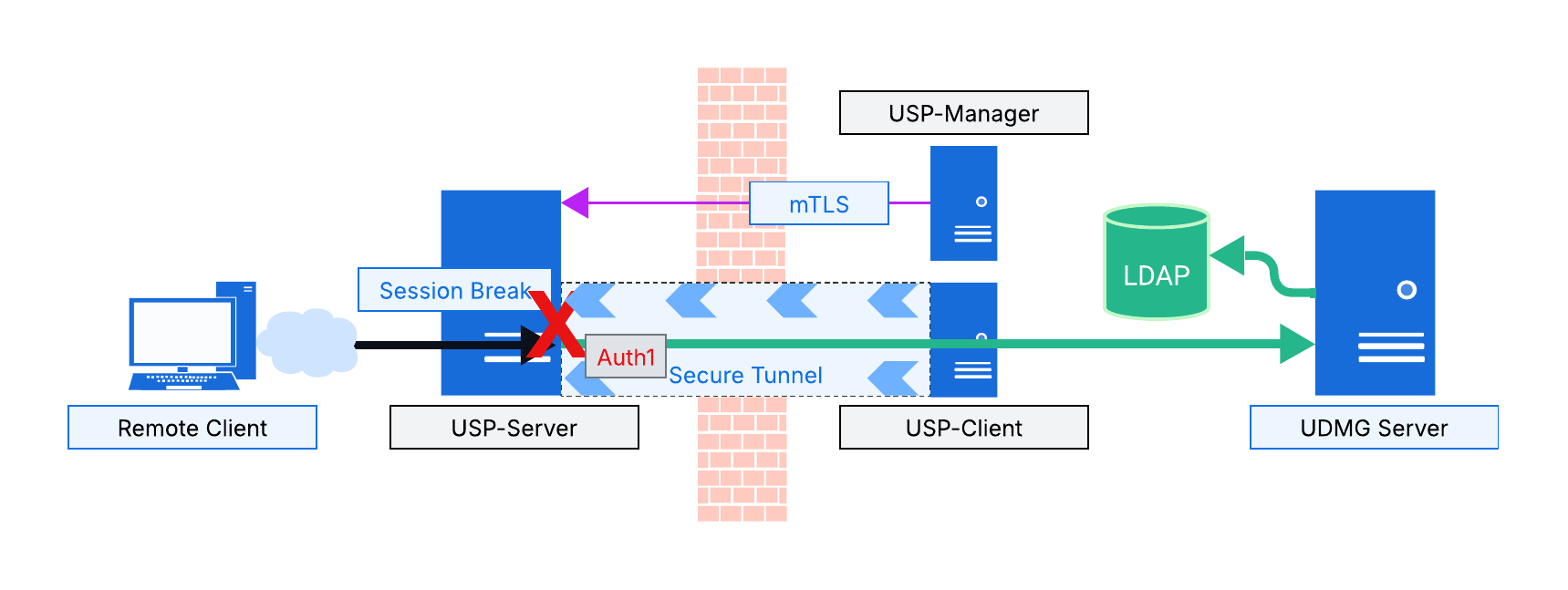
As in Model 1, all three USP components are deployed (see Note on Minimal Installations) and the USP Server is configured via the USP Manager. However, in this model, the USP Server is not performing authentication.
The USP Server still terminates the inbound connections and acts as a reverse proxy, maintaining the session break architecture. It then connects to the internal UDMG Server in the LAN via a secure tunnel established by the USP Client and relays (passes through) the client-provided credentials for authentication with UDMG Server.
The UDMG Server receives and authenticates the credentials. If authentication fails, the USP Server relays the failure back to the external client and terminates the connection.
| Use Case | Benefits | Drawbacks |
|---|---|---|
| Environments that prioritize performance or have fewer concerns about exposing authentication attempts to the back end. |
|
|
Note on Minimal Installations
While USP can be deployed with just the USP Server and USP Manager (omitting the USP Client), this configuration is only appropriate in sandbox environments where security is not a concern and firewall restrictions are not imposed.
Without the USP Client, the USP Server must open a direct path through the firewall to internal systems, discarding many security benefits of the reverse proxy architecture.
Optional Deployment Model
The following model is supported by USP but not recommended for most production use cases due to its weak security posture.
Model 3: Double Authentication with Dedicated Credentials
In this setup, USP Server authenticates external incoming connections, but does not relay their credentials to UDMG Server. Instead, it uses a fixed credential set. This effectively anonymizes user identity beyond the proxy.
| Use Case | Benefits | Drawbacks |
|---|---|---|
Specific business requirements that can withstand identity abstraction at the backend systems. |
|
|
Other Models
The deployment models described above represent the most common and practical configurations. However, USP is highly flexible and can support additional variations tailored to specific technical or business requirements.
For guidance on alternative deployment models and their trade-offs, please contact our team.